- Blog, Cyber Security
- Published on: 19.12.2024
- 11:56 mins
OT Security: Get Your Company Fit for Industry 4.0
The increasing networking of software and hardware in industry has led to companies becoming ever-more dependent on digital systems. At the same time, the threats from cybercrime are continuously increasing. In the third quarter of 2024 alone, 422 million user accounts were exposed. And these figures don’t include the high number of unreported cases. According to official figures, the financial damage from cybercrime recently amounted to over 200 billion euros a year. These alarming developments show how important it is to protect your company against digital threats. As such, cybersecurity in general and operational technology security (or OT security for short) in particular are more than just a technical requirement; they should be a strategic priority to prevent companies from financial damage and a loss of trust. A robust cybersecurity strategy is the key to future-proofing systems, particularly within the context of Industry 4.0, where machines, systems, operating systems, and data are all intelligently connected.
In this article, you will discover how to protect your company from cyberattacks, how to increase your OT security, and how MHP can support you through the process.
IT Security & OT Security: What Is the Difference?
Information technology security (IT security) focuses on security when processing and managing data. IT primarily refers directly to computers, devices, network devices, or servers.
By contrast, OT security – or operational technology security – focuses on the security of machinery, other production hardware, and industrial control systems (ICS). In the past, these components were only accessible within the physical space. But this is changing. As a result of Industry 4.0. Production technologies are becoming increasingly interlinked and connected to the internet. As such, OT security needs to ensure that these digital connections are secure too.
Industrial control systems, or ICS for short, serve to collate and evaluate data from different sensors in production. ICS visualizes key information and uses this information to take direct measures based on the data. For example, an ICS can regulate a control valve based on the data it receives.
Industry 4.0 – Networking Opens Up New Opportunities for Attack and More Risks of Loss
Digitalization and the increasing level of networking resulting from Industry 4.0 provide immense opportunities for companies, but they also bring with them a great deal of risk. The complex infrastructure that is created when machines, systems and data interact digitally demands a high level of security. In addition, the long service life of operating technology presents decision-makers with major security challenges. Although the old systems are tried and tested, increasing networking can lead to entire production lines failing. Integrating OT with IT presents both opportunities and a high level of risk when it comes to networking and security.
Cybersecurity: Increasingly important and increasingly urgent
Cybercrime has caused enormous economic damage in recent years. Damage amounting to more than 10 trillion US dollars is predicted by 2025. Besides the economic losses, primarily caused due to failures, malfunctions and damage to technical systems, there are also immaterial losses such as a loss of customer trust or reputational damage.
A cyberattack can also cause technical damage that goes far beyond simple system malfunctions. Databases can be destroyed, valuable information irretrievably lost, and trade secrets can be stolen and leaked. In some cases, manipulated machines can even cause physical damage to the infrastructure.
Specific cybersecurity risks relating to Industry 4.0
Industry 4.0 promises greater flexibility and customization, faster processing times, and higher quality – but these benefits are offset by a significantly higher risk of cyberattacks. In the next section you can read more about the key risk factors associated with Industry 4.0.
Increased complexity and networking
The industrial landscape is becoming more and more complex due to the networked machines, sensors, and IT systems. Each networked device poses a potential risk for cyberattacks, especially when they are connected to the internet. As Industry 4.0 is based on the interoperability between different systems, the area at risk of attack increases considerably. Furthermore, the variety of interfaces, operating systems, and communication protocols makes it difficult to monitor and protect all of the interfaces.
An increase in potential entry points
Networked systems and the Internet of Things (IoT) create additional points of attack. Each interface in a networked device – be it a machine, a sensor, or a piece of production software – can be exploited by cybercriminals. In the worst case, attackers can compromise the entire chain of production via a device with weak protection, leading to machine failures, damage to technology, and malfunctions across the entire company.
High susceptibility to failure in the event of a cyberattack
The close integration of production systems, operating technology, and information technology means that an attack can have serious consequences on the entire operation. A targeted cyberattack can paralyze machines, disrupt production processes, or bring entire networks to a standstill. The resulting economic damage is often huge. Production downtime, data loss, and the need to restore damaged systems often leads to immense costs.
Potential damage in numbers
To give you an idea of the scale of the potential technical, economic, and reputational damage, we have compiled some real-life examples with the corresponding figures:
Economic damage
Direct economic losses resulting from cyberattacks often include production downtime and the cost of recovery processes and security measures. The global average costs of a data breach in 2024 was 4,88 million US dollars.
Reputational damage
The failure of entire production and supply chains and the loss of production data or trade secrets can cause lasting damage to the trust held by your partners and customers. This often has lasting financial consequences. This is especially true for listed companies, where a loss of trust is reflected in a falling share price. In 2022, a cyberattack on the company Hensoldt led to a 5.7 percent fall in the share price in just one day. Varta also recorded a sharp drop of 5.6 percent in its share price following a similar attack in 2024.
Technical damage
Manipulated production facilities, destroyed databases, and lost information have the potential to paralyze operations for weeks or even months. If you suffer a successful ransomware attack, for example, the downtime usually lasts a very long time.
In order to get a handle on these types of threats, companies looking to successfully transition to Industry 4.0 need a comprehensive OT cybersecurity strategy.
NIS-2 Directive, Machinery Directive, and the Cyber Resilience Act: The Laws Governing Cybersecurity
The importance of cybersecurity is underlined by EU Directive 2022/2555 (NIS-2 Directive). This bill was passed by the European Parliament and the European Council on 14th December 2022 and, along with the Machinery Directive and the EU Cyber Resilience Act (CRA), contains measures for a high common level of cybersecurity across the European Union.
The NIS-2 Directive states that companies with over 50 employees or an annual turnover or balance sheet of over 10 million euros must take numerous measures to protect their digital infrastructure.
The Machinery Directive 2006/42/EC has been regulating the different aspects of health and safety relating to machinery in the EU since 2009. The directive sets out the requirements for safety and protective devices, risk assessments and conformity assessment procedures, amongst other things. It will be replaced by the Machinery Directive (EU) 2023/1230 from 2027. This new regulation will extend the requirements to incorporate parts of cybersecurity, artificial intelligence, and machine learning. In addition, the new Machinery Directive covers software and other digital components.
The CRA further expands upon the cybersecurity requirements. The regulation obliges companies to implement security measures for products that are connected to each other and/or the internet. This applies to both hardware and software.
The Challenges Facing Industry 4.0 Protection Strategies at All Levels
In view of the increasing networking of different assets within your company, it is important to be aware of the possible weak spots within the OT and IT infrastructure and to secure these vulnerabilities with effective measures. While the aims of classic IT security focus on confidentiality, integrity, and availability; safety is a key focus within the field of OT security. Effective protective measures are key, particularly within the context of Industry 4.0 and the increasing security requirements in IT.
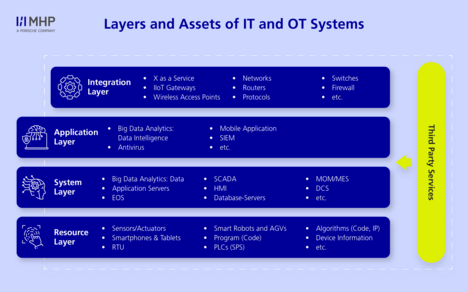
In order to develop effective and sustainable protection strategies, MHP created a vulnerability model with the help of the ENISA Asset Taxonomy (European Union Agency for Network and Information Security. This model assigns the various assets to the four different layers of the IT system architecture:
Resource layer
The resource layer encompasses a company’s physical and digital resources. It includes machinery, sensors, and even personnel. In this layer, data that is crucial for production processes is collated and processed. Protecting these physical and digital resources from manipulation is one of the greatest challenges. Attacks on IoT devices (e.g. sensors) or social engineering attacks on employees can have a significant impact on production. Many IoT devices and sensors are still insufficiently protected against cyberattacks, which in turn poses a considerable security risk.
System layer
The system layer forms the backbone of IT infrastructures and encompasses core systems such as databases, production controls, and human machine interfaces (HMI). These systems are crucial for the operation and control of production processes. Vulnerabilities in the system layer can lead to attackers taking control of critical production processes, leading to production downtimes, manipulation, or data losses. One of the greatest challenges here is that many of these operating technologies were originally operated in isolation and are now facing new threats as they become more interconnected.
Application layer
This layer lies above the system layer and encompasses user-centric applications that interact directly with production systems and data sources and that allow the user to intuitively use the data available in the company. In terms of Industry 4.0, this often includes applications for SIEM (security information and event management), big data analytics, or mobile applications providing insights into production processes. The flexible adaptability of these systems makes them a preferred target for cyberattacks, as attackers can exploit vulnerabilities in the software or insecure configurations. A successful attack on this layer can lead to serious disruptions in data processing and production control.
Integration layer
The integration layer relates to the connection between different systems and data sources, which are of central importance in Industry 4.0. Here we are talking about communication between machines, production systems, and external services. The challenges for this layer predominantly concern the security of the data transfers. Attackers can exploit weaknesses in protocols or unsecured communication channels in order to gain unauthorized access to systems. The fact that many of these protocols were not developed with a focus on cybersecurity is important here.
The challenges when it comes to implementing protection strategies for Industry 4.0 are complex and require a holistic security strategy. Your company must consider the different layers of the OT and IT system architecture and ensure that both the physical and digital infrastructure are protected against cyber threats. The increasing complexity and networking of systems requires an effective approach when it comes to cybersecurity.
MHP’s Three-Phased Approach to Secure Your Company Against Cyberattacks
The measures mentioned above can be implemented quickly. However, this is just the first step in developing and establishing a viable OT cybersecurity concept that addresses your company’s individual requirements. As a renowned partner in this field, MHP has many years of experience and broad expertise in cybersecurity and Industry 4.0. As such, MHP is perfectly placed to protect your company against cyberattacks. We provide comprehensive end-to-end support and are on hand to assist, from identifying vulnerabilities and prioritizing assets to defining and implementing measures:
Asset analysis
An effective security strategy is based on the precise analysis of your company’s assets. When it comes to Industry 4.0, we are not just talking about machinery and physical resources, but also IT systems, software applications, and networks.
The asset analysis identifies the components with a critical function that could represent potential targets for attack. We incorporate the requirements set out in the CRA, the Machinery Directive, and the NIS-2 Directive.
Identifying vulnerabilities and prioritizing assets
Once the assets have been analyzed, we identify the specific weak points of each asset. These vulnerabilities may manifest in different areas of the systems:
- Physical vulnerabilities: Attackers could penetrate the system via unprotected devices like sensors or actuators.
- Digital vulnerabilities: Inadequately secured networks or outdated software with known security vulnerabilities provide opportunities for attack.
- Human vulnerabilities: Employees could contribute to unwanted security vulnerabilities through social engineering attacks or phishing.
Resources that are particularly vulnerable to attacks and that could cause the largest potential damage in the event of a failure or an attack are prioritized.
Ascertaining measures
Once the vulnerabilities have been identified and prioritized, MHP takes targeted action. The approach is governed by the relevant guidelines, including the NIS-2, Machinery Directive, and the CRA. Effective measures may include:
- Securing communication protocols in the integration layer: Secure protocols and encryption should be used to minimize vulnerabilities in the protocols used for machine communication.
- Patch management in the system layer: Software updates and patches should be performed regularly to close known security vulnerabilities in production systems.
- Access controls in the application layer: Implementing access restrictions and multi-factor authentication can help to ensure that only authorized users have access to critical systems.
- Physical security in the resource layer: Security measures such as cameras and access restrictions prevent unauthorized access to physical systems.
Adopting a structured approach can considerably reduce the risk of cyberattacks and can allow you to better protect your operational technology and IT systems against the complex threats facing Industry 4.0. MHP is here to help you throughout this process.
Effective Protection from Cyberattacks with MHP
The increasing digitalization and networking caused by Industry 4.0 offers great opportunities to companies but it also increases their vulnerability to cyberattacks. The increasing number of cyberattacks and the associated economic damage underline the importance and urgency of cybersecurity. However, by performing a detailed analysis of their own assets, by identifying vulnerabilities, and by implementing targeted security measures, companies can effectively protect their digital infrastructure.
MHP provides tailored solutions for your specific use case and is here to support you when it comes to developing and effectively implementing the right protection strategy for your company.
FAQ
OT security protects a variety of machines and systems that control the physical processes in industry, energy, manufacturing, and transport. The focus is on providing protection against manipulation and cyberattacks. As such, an effective OT security strategy prevents security risks and economic damage.
Cybersecurity is the protection of computer systems, networks, and data against digital attacks, unauthorized access, and cyber threats. It encompasses technologies, processes, and measures aimed at safeguarding the confidentiality, integrity, and availability of information in the digital world.
Cybersecurity includes topics like network security, application security, information security, and cryptography. Areas such as identity and access management, security policies, risk management, and incident response are also part of the parcel of cybersecurity. In addition, it encompasses current topics like cloud security, mobile security, and protecting the Internet of Things (IoT).